- Home
- Services
- Managed IT Security
- Two Factor Authentication
Two Factor Authentication – Protect the Security of Online Accounts
Understandably, cybercriminals have driven toward our digital accounts, given how much of our lives take place online. They suddenly have an excessive number of passwords to remember when they open more and more accounts. It may result in password recycling, the worst-case scenario for security professionals. An additional layer of protection called two-factor authentication can assist address the problem of using weak or frequently used passwords.
Geek Force USA guides the best multi-factor authentication solution for your business in cyber security. Our staff drives your security initiatives. In collaborating with us, we do more than merely safeguard your data. Our professionals assist you in maintaining an edge over the competition and creating an organizational culture that prioritizes cyber security.
Function of Two-Factor Authentication
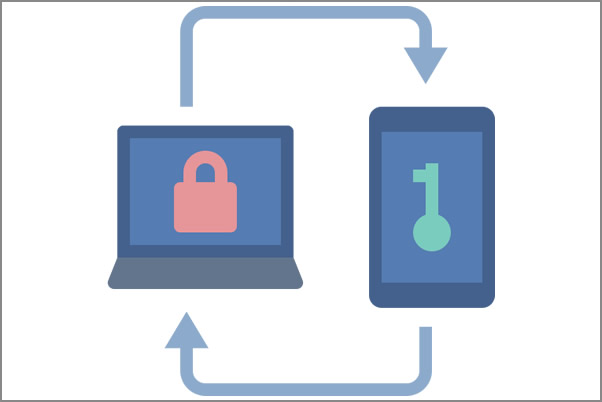
Users should prove that they are who they claim to be by using two-factor authentication. In this manner, accessing a system or account will be significantly more difficult, if not impossible, even if someone has access to another user’s password. Facebook, Twitter, or Instagram users who have enabled two-factor authentication might be familiar with this technique. After the user enters their password, a one-time password or code will be sent to the device or account of their choice (usually via email, SMS, or an automated phone call). To completely access the account, users must enter that code, preventing access by unauthorized users.
If a computer or other device is trusted and well-known, users may authorize it using this approach to avoid requiring two-factor authentication. Similarly, the account can recognize attempts to log in from unknown or unidentified locations or devices and need a one-time code.
More complicated forms of two-factor authentication are also available, ideally suited to users and businesses with highly stringent security requirements. Biometric scanners, which look for a recognizable feature like a fingerprint, face, or retina, can serve as the second layer of security. Even though it might sound like something from a science fiction movie, many modern cellphones unlock using a fingerprint or facial recognition system!
Another second factor that is gaining popularity as it spreads from the area of IT businesses to the general public is security keys. Users must enter a password and a security key through a USB connection to acquire full access. Users who use this method must ensure they are in actual possession of the key. Whatever technique you decide on, two-factor authentication is relatively easy to deploy and offers a wide range of benefits beyond basic security, whether for yourself, your company, or another organization.
Two-Factor Authentication Benefits
Increased security
Boost productivity and flexibility
Lower costs for managing the help desk and security
Minimize fraud and create secure online connections




